Thick Client (Desktop) Application Penetration Testing – Part-1
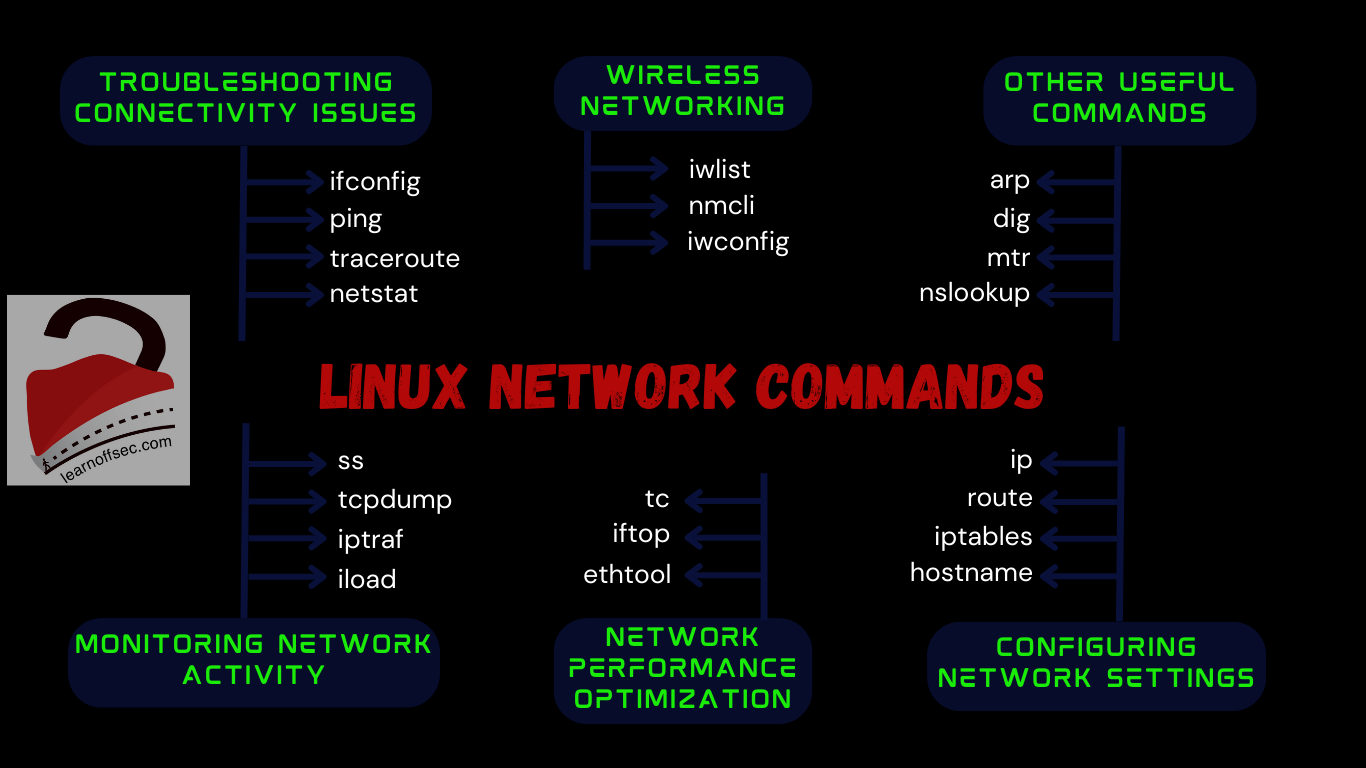
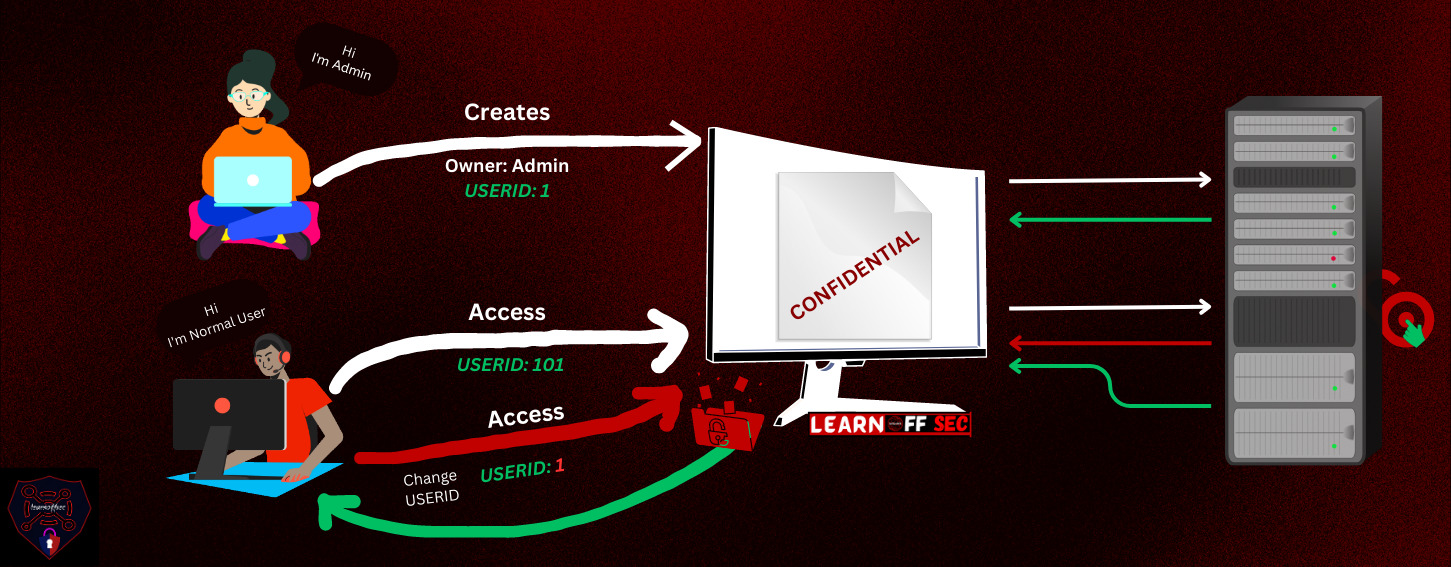
INFORMATION GATHERING Using the tool CFF Explorer Using the SysInternal Suites Let’s start … Using the Tool Wireshark Using the Tool ProcMon (Login Credentials in Registry Entry) TRAFFIC ANALYSIS Traffic Analysis using Wireshark Filter technique 1 Filter technique 2 Using Tool Echo Mirage