Welcome to the exciting world of Docker! If you’re a fan of containers and their many benefits, you’ll love this post on unsegregated container networks in Docker.
But what exactly is an unsegregated docker container network, you ask? Think of it like a bustling city with different neighborhoods, each with its own unique character and charm. Now imagine those neighborhoods as containers in Docker, each with its own isolated environment.
However, just like how the different neighborhoods in a city need to communicate and work together, so too do the containers in Docker. That’s where unsegregated container networks come into play, allowing containers to communicate and collaborate effortlessly.
So sit back, grab a cup of coffee/tea and get ready to learn all about unsegregated container networks in Docker!
Understanding Segregated Container Networks
Definition of Segregated Container Networks
A segregated container network also known as a isolated container network is a network configuration in which each container is isolated from the others & can only communicate with the host or other containers through a specific network connection. This type of network configuration is often used in environments where security and stability are a concern.
Advantages of Segregated Container Networks
Segregated container networks have several advantages, including;
- Improved security: By isolating containers, a segregated container network can
reducethe risk of security vulnerabilities andpreventunauthorized access to sensitive information. - Better resource management: Segregated container networks can help ensure that each container has the resources it needs, such as
CPUandMEMORYwithout affecting the performance of other containers. - Easier troubleshooting: If a problem occurs in one container, it
won't affectthe performance of other containers on the network. This makes it easier to identify and resolve issues.
Limitations of Segregated Container Networks
However, segregated container networks also have some limitations, including:
- Limited communication: Containers in a segregated network are limited in their ability to communicate with each other, which can make collaboration between containers more difficult.
- Increased complexity: Setting up a segregated container network can be
more complexcompared to an unsegregated network, which can make it difficult for developers to manage and maintain. - Reduced efficiency: The restrictions on communication between containers can make it more difficult for containers to work together & share information, leading to reduced efficiency.
Real–World Scenario
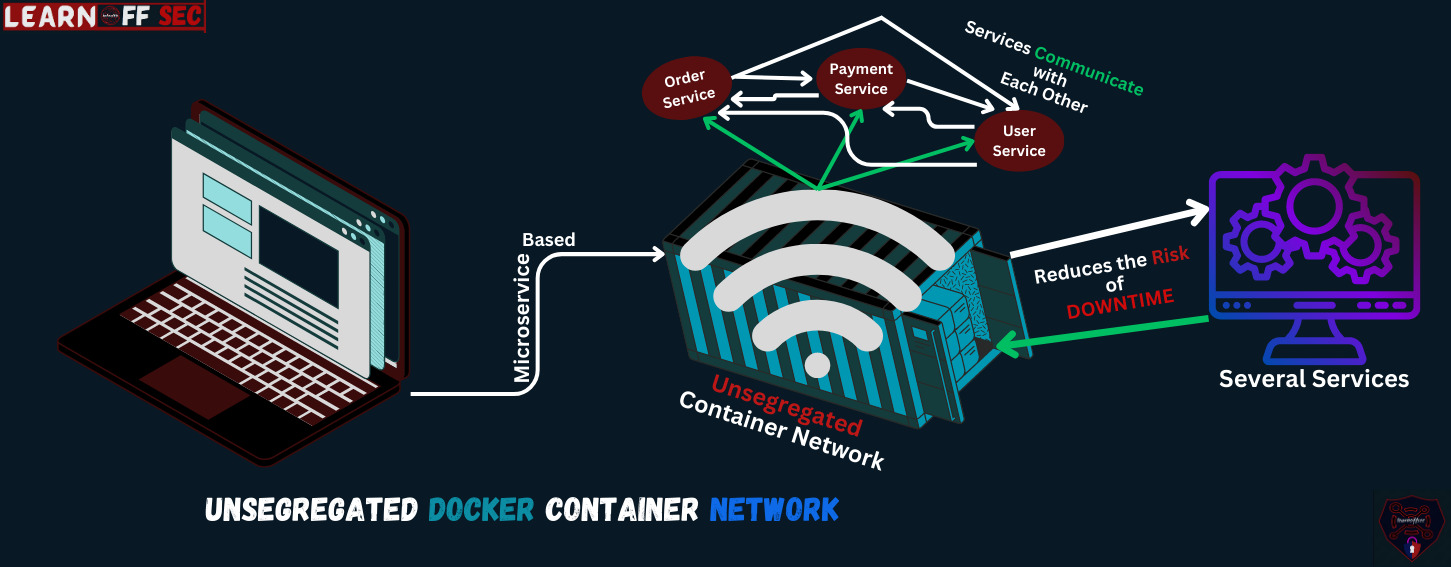
You are a software developer building a microservice-based web application. Your application consists of several services, such as an user service, a payment service & an order service, each running in its own container. To communicate with each other, these services need to be on the same network.
The Problem:
You have been using segregated container networks for your services but you have recently run into performance issues. The communication between the services is slow and you are experiencing frequent downtime.
The Solution:
You decide to switch to an unsegregated container network in Docker. This allows your services to communicate with each other more efficiently and reduces the risk of downtime.
Create an unsegregated network
docker network create my-unsegregated-network
Launch the user service
docker run -it --name my-user-service --network my-unsegregated-network my-user-service-image
The payment service Lunch
docker run -it --name my-payment-service --network my-unsegregated-network my-payment-service-image
Launch the order service
docker run -it --name my-order-service --network my-unsegregated-network my-order-service-image
With this code, you can see how easy it is to launch services in an unsegregated container network in Docker. By connecting these services to the same network they can communicate with each other efficiently & provide a seamless experience for your users.
Local IP Address – Docker
The local IP address of a Docker container can be obtained using the following command:
docker inspect --format='{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' container_name_or_id
Note that this command will return the IP address of the first network attached to the container. If the container is connected to multiple networks, you may need to modify the command to return the desired IP address.
Network Scan – Docker
A network scan in Docker refers to the process of finding active hosts & open ports in a network. This can be useful for network administrators to monitor network security & identify potential vulnerabilities.
To perform a network scan in Docker, you can use a tool such as Nmap which is a popular open-source network scanner. You can run Nmap in a Docker container to perform a scan of a network. For example; the following command will run a Nmap scan of a network using a Nmap Docker image:
docker run -it --rm --network host -v $(pwd):/data nmap -sS -p 0-65535 [target_ip_or_hostname] -oX /data/scan-result.xml
In this command, the --network host option is used to connect the Nmap container to the host’s network, allowing it to perform the scan. The -v $(pwd):/data option mounts the current directory as a volume in the container, so that the scan results can be saved as a XML file in the host file system. The -sS option specifies the type of Nmap scan to perform and the -p 0-65535 option specifies the range of ports to scan.
Keep in mind that network scanning can be a sensitive operation & you should only perform network scans in Docker with the proper authorization and in accordance with your organization’s network security policies.
Setting Up an Unsegregated Container Network in Docker
Overview of the Setup Process
Setting up an unsegregated container network in Docker is a relatively straightforward process. The process involves creating a new network and then connecting containers to that network. This allows the containers to communicate freely with each other & and share resources as needed.
Step-By-Step instructions for setting up an unsegregated container network
Here are the steps to set up an unsegregated container network in Docker:
- Create a new network: To create a new network in Docker, you can use the following command:
docker network create my-network
- Launch your containers: Launch your containers and connect them to the new network using the
--networkflag:
docker run -it --name my-container --network my-network ubuntu:18.04
- Test connectivity: To test connectivity between containers, you can use the
ping command. For example; you can launch another container and use the following command to ping the first container;
docker run -it --name my-container2 --network my-network ubuntu:18.04 ping my-container
Example code to help illustrate the setup Process
Here is an example of how to set up an unsegregated container network in Docker:
Create a new network
docker network create my-network
Launch the first container and connect it to the new network
docker run -it --name my-container1 --network my-network ubuntu:18.04
Launch the second container and connect it to the new network
docker run -it --name my-container2 --network my-network ubuntu:18.04
Test connectivity by pinging the first container from the second container
docker exec -it my-container2 ping my-container1
This code creates a new network named ‘my-network‘ and launches two containers, ‘my-container1‘ and ‘my-container2‘. Both containers are connected to the ‘my-network‘ network allowing them to communicate freely with each other. The code then tests connectivity between the two containers by using the ‘ping‘ command.
Advantages of Unsegregated Container Networks
Explanation of the Benefits of Unsegregated Container Networks
Unsegregated container networks offer several benefits over segregated container networks, including;
- Improved communication: Containers in an unsegregated network can communicate freely with each other, which can lead to improved collaboration and efficiency.
- Simplified setup: Unsegregated container networks are typically easier to set up and manage compared to segregated networks, making them a good choice for developers who want to streamline their work.
- Increased flexibility: Unsegregated networks provide greater flexibility for containers to communicate and share resources making them
well-suitedfor complex projects.
Comparison to Segregated Container Networks
When compared to segregated container networks, unsegregated networks offer greater flexibility and improved collaboration between containers. While segregated networks can offer improved security & better resource management, they can also limit the communication between containers and make it more difficult to troubleshoot issues.
Real-World use cases of Unsegregated Container Networks
Unsegregated container networks can be used in a variety of real-world scenarios, such as;
- Microservices architecture: In a microservices architecture, multiple services work together to provide a complete solution. Unsegregated container networks make it easier for these services to communicate and share information leading to improved efficiency and scalability.
- Distributed systems: Distributed systems often require multiple components to communicate and work together in
real-time. An unsegregated container network can provide the necessary communication channels for these components to collaborate. - Cloud-based applications: Cloud-based applications often require multiple containers to communicate and share resources. An unsegregated container network can provide the necessary infrastructure for these containers to collaborate and achieve their goals.
Managing & Maintaining an Unsegregated Container Network
Overview of the Management Process
Managing and maintaining an unsegregated container network in Docker requires ongoing attention & effort. It is important to ensure that the network continues to function as expected & to address any issues that may arise.
Best Practices for Managing & Maintaining an Unsegregated Container Network
Here are some best practices for managing and maintaining an unsegregated container network in Docker;
- Monitor network performance: Regularly monitor the performance of the network to identify any issues and address them promptly.
- Keep containers updated: Make sure to keep your containers updated to ensure they are running the latest version of the software.
- Limit the number of containers: Avoid overloading the network with too many containers as this can slow down performance & create other issues.
- Implement security measures: Implement security measures such as
firewalls,encryption, andaccess controlto protect the network from malicious attacks.
Troubleshooting Tips for Common Issues
Here are some troubleshooting tips for common issues that may arise when managing an unsegregated container network in Docker;
- Container connectivity issues: If containers are
unableto communicate with each other, check that they are connected to thesame networkand that there areno firewallsblocking their communication. - Slow network performance: If the network is running slowly, try limiting the number of containers on the network and checking for any network
congestion. - Inconsistent network behavior: If the network is behaving
erratically, check for any misconfigurations or issues with the underlying infrastructure.
Monitor network performance
docker network inspect my-network
Keep containers updated
docker pull ubuntu:18.04 docker restart my-container1 docker restart my-container2
Limit the number of containers
docker network prune
Implement security measures
docker run -it --name my-container1 --network my-network --cap-add=NET_ADMIN ubuntu:18.04 docker run -it --name my-container2 --network my-network --cap-add=NET_ADMIN ubuntu:18.04
This code explains; how to keep containers updated, limit the number of containers on the network & implement security features like giving the containers ‘NET ADMIN‘ capabilities.
Vulnerabilities of Unsegregated Container Network
Here are some of the vulnerabilities in an unsegregated container network:
- Container Breakouts; To prevent container breakouts you can use the
--security-optoption in Docker to set the container’s security profile. For instance; you can use the below command to run a container with theseccompprofile that limits the system calls available to the container;
docker run --security-opt seccomp=<path-to-seccomp-profile.json> <image-name>
- Network Exposure: To limit network exposure, you can use the
--networkoption in Docker to specify the network mode for the container. For example; you can use the following command to run a container in thehost network modewhich restricts the container’s access to the host’s network;
docker run --network host <image-name>
- Container Hijacking: Use secure authentication techniques such as employing
encrypted keysfor container authentication, to prevent containerhijacking. Also, you may define the user that the container runs as using the—useroption in Docker which can aid in preventing unauthorized access to the host system.
docker run --user <user-name> <image-name>
- Lack of Network Segmentation: To implement network segmentation you can create multiple user-defined networks in Docker and connect containers to the appropriate network. For instance; you can use the following command to create a new network and connect a container to it;
docker network create <network-name> docker run --network <network-name> <image-name>
Mitigation – Unsegregated Container Network
When it comes to unsegregated container networks in Docker, it’s important to be aware of potential vulnerabilities and to implement security measures to mitigate the risk of attack. Here are five common vulnerabilities in unsegregated container networks and examples of how to mitigate them:
- Container Escapes: Containers can potentially escape their intended environment & gain access to the host system. This can be mitigated by using
namespaces & cgroupsto limit the resources available to containers.Example
docker run --rm -it --security-opt=seccomp=unconfined alpine sh
- Unsecured Network Connections: Unsecured network connections can allow attackers to
interceptandmanipulatenetwork traffic. This can be mitigated by usingencrypted connections& bysetting up firewallsto restrict access to the network.Example
docker run -d --name some-postgres -e POSTGRES_PASSWORD=yoursecretpassword postgres docker run -it --link some-postgres:postgres --rm postgres sh -c 'exec psql -h "$POSTGRES_PORT_5432_TCP_ADDR" -p "$POSTGRES_PORT_5432_TCP_PORT" -U postgres'
- Unsecured Container Data: Containers can store sensitive data that can be accessed by
unauthorizedusers. This can be mitigated by properly securing the data, using encryption & regularly backing up the data.Example
docker run -it --rm -v /path/to/data:/data busybox ls /data
- Unsecured Container Images: Unsecured container images can contain malicious code that can compromise the system. This can be mitigated by properly verifying the source of the images & by using
signed images.Example
docker run -it --rm ubuntu:18.04 apt-get update docker run -it --rm ubuntu:18.04 apt-get upgrade
- Unsecured Host System: An unsecured host system can provide a
backdoorfor attackers to access the container network. This can be mitigated by properlysecuringthe host system, using strong passwords & regularly updating the system.Example
docker run -it --rm --privileged --pid=host justincormack/nsenter1
By following these mitigation steps & examples, you can help secure your unsegregated container network in Docker & minimize the risk of potential security vulnerabilities.
Summary
In last, unsegregated container networks in Docker offer numerous benefits compared to segregated container networks. Unsegregated networks provide better network performance, increased security & the ability to easily manage and maintain a large number of containers. They also make it easier for containers to communicate with each other, which can be especially beneficial for applications that require real-time communication.
When it comes to choosing a container network, unsegregated networks are a great choice for those looking to take advantage of the benefits of Docker. They are easy to set up, manage and maintain & they provide a high level of security and network performance.